Key Takeaways
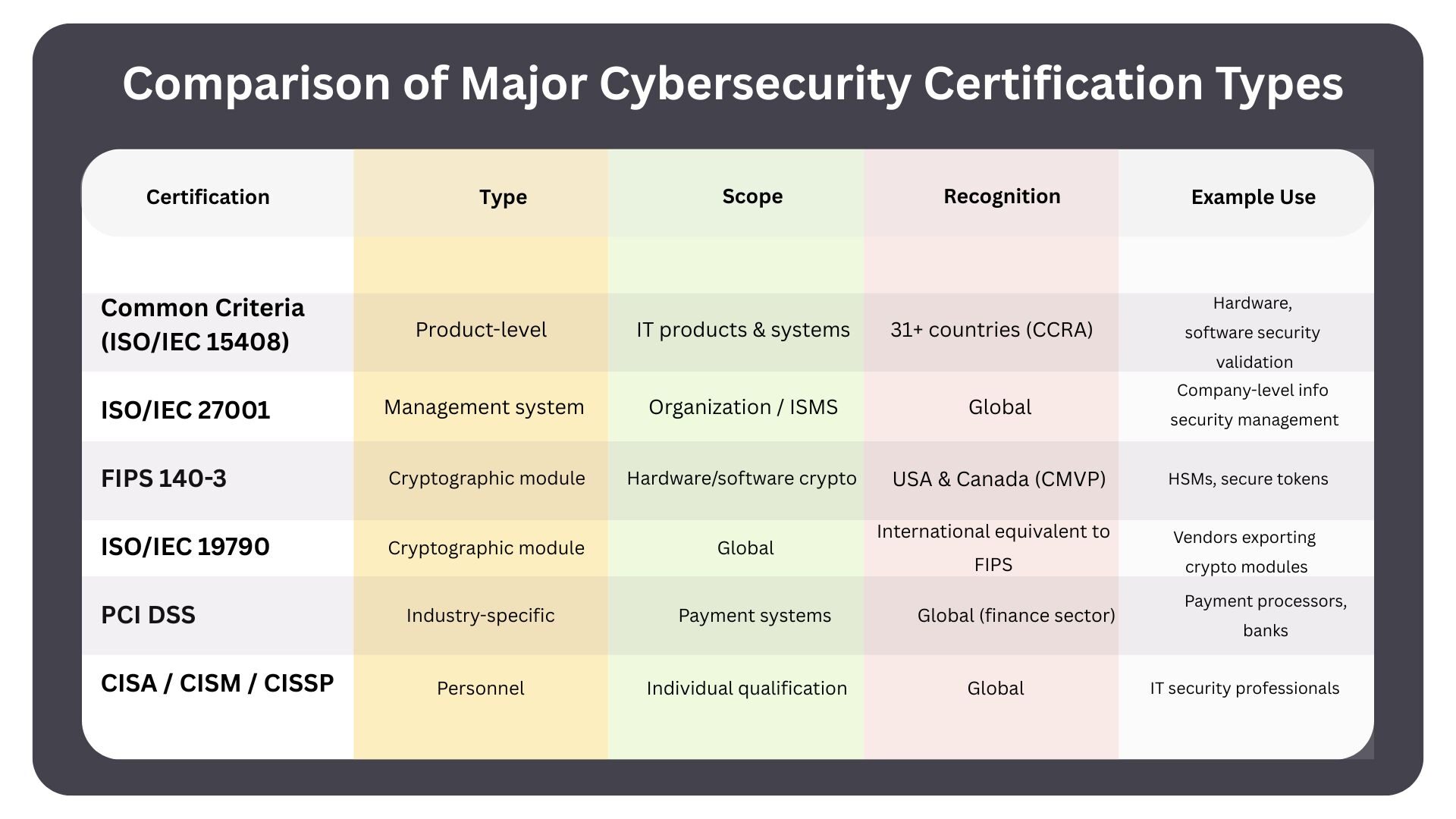
- Common Criteria (ISO/IEC 15408) is a widely recognized international framework for product-level security evaluation and certification.
- ISO/IEC 27001 certifies information security management systems (ISMS) at the organizational level—not individual products.
- FIPS 140-2/3 provides specialized validation for cryptographic modules (e.g., HSMs, tokens).
- Evaluation Assurance Levels (EAL1–EAL7) in Common Criteria indicate the depth and rigor of testing and verification.
- Mutual recognition arrangements mean Common Criteria certificates issued in one member country are recognized by many others, reducing duplicate testing.
When organizations across industries seek to protect digital assets, a critical question arises: Which certifications are internationally recognized for computer security products? With evolving threats and growing compliance expectations, understanding globally accepted schemes helps teams make informed, efficient procurement and design decisions.
This guide explains the product-focused international standard (Common Criteria), how it compares with management-system and crypto-specific certifications, and how to choose what fits your use case.
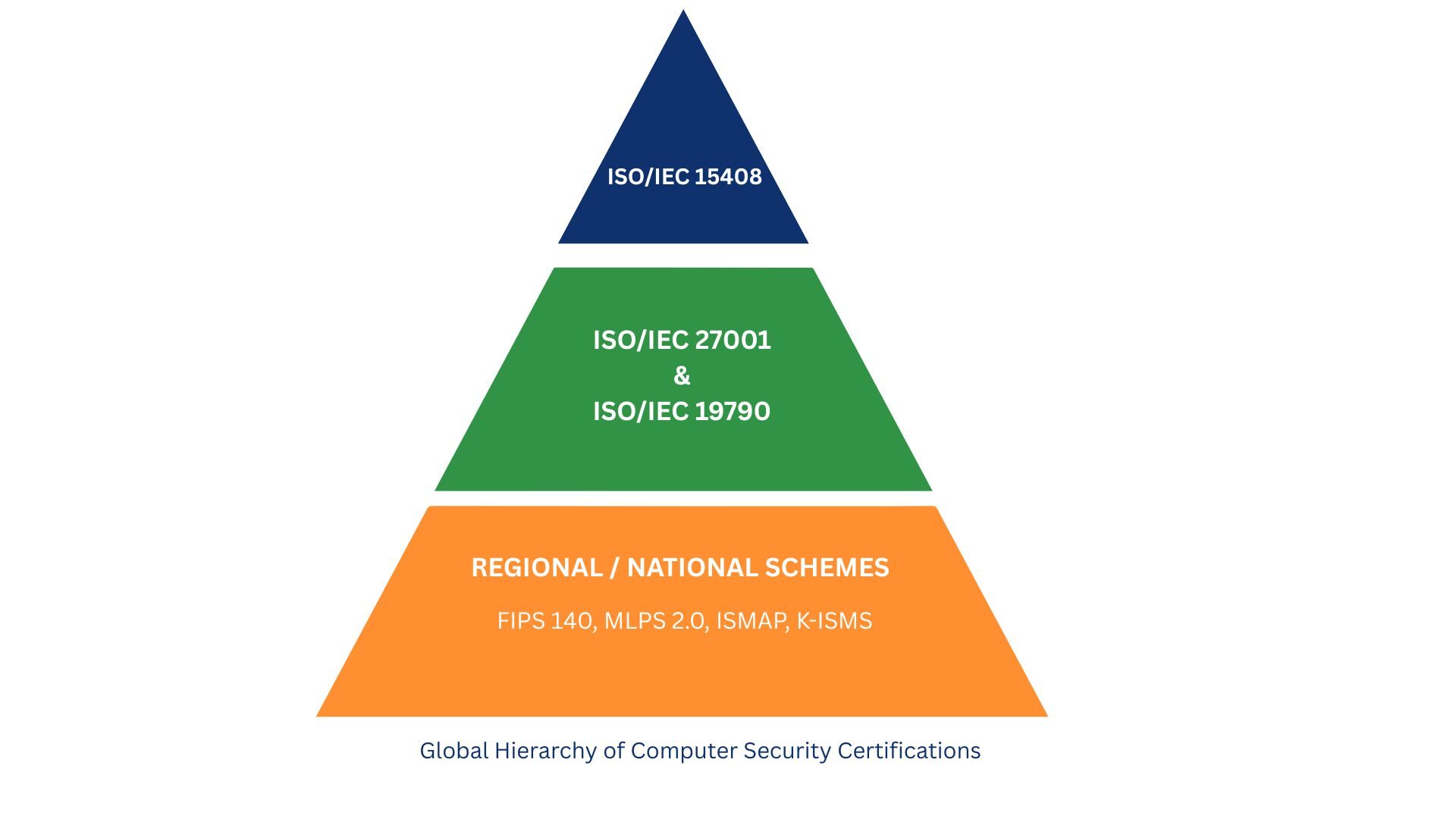
The De facto Global Product Standard: Common Criteria (ISO/IEC 15408)
Common Criteria (CC) is an internationally recognized framework for evaluating and certifying the security properties of IT products and systems. It harmonized earlier national schemes (e.g., the U.S. Orange Book/TCSEC, Canada’s CTCPEC, Europe’s ITSEC) and was standardized as ISO/IEC 15408.
Today, CC certificates benefit from mutual recognition among participating countries via the Common Criteria Recognition Arrangement (CCRA), making it one of the most broadly accepted product-level certification frameworks.
Structure of the Standard
- Part 1: Concepts and model
- Part 2: Security functional requirements (what the product must do)
- Part 3: Security assurance requirements (how convincingly claims are demonstrated)
Protection Profiles & Security Targets
- Protection Profiles (PPs): Community-defined requirements for a product category (e.g., firewalls, smart cards).
- Security Target (ST): Vendor-specific scope and claims for the product being evaluated—the “contract” for the evaluation.
Evaluation Assurance Levels (EAL1–EAL7)
EALs reflect the rigor of the evaluation:
- EAL1: Functionally tested (baseline assurance)
- EAL2–EAL3: Structurally/methodically tested (common for commercial products)
- EAL4: Methodically designed, tested, and reviewed (frequent target for COTS)
- EAL5–EAL7: Semi-formal to formal verification (for high-assurance, specialized contexts)
Most commercial vendors target EAL2–EAL4 as a practical balance of assurance, cost, and time.

Typical Product Categories
- Operating systems (enterprise variants)
- Network security devices (firewalls, VPN gateways, IDS/IPS, NAC)
- Smart cards & secure tokens (eIDs, payments, ePassports; often with specific PPs)
- Databases & enterprise security software (e.g., SIEM, PAM, encryption)
- Industrial & OT security components (growing with digitization)
Other Important International Standards
While Common Criteria focuses on product assurance, several complementary standards address organizational and cryptographic security.
ISO/IEC 27001 — Management Systems (ISMS)
- What it certifies: An organization’s ISMS, not a product.
- Focus: Risk management, policies, controls, continual improvement.
- Use it when: You need to demonstrate organizational security governance and process maturity to customers, partners, or regulators.
- Relation to CC: Complementary—buyers often look for capable, certified products and a certified ISMS.
FIPS 140-2 / FIPS 140-3 — Cryptographic Module Validation
- What it certifies: Cryptographic modules (software, firmware, hardware).
- Scope: Levels 1–4 for physical security, roles/authentication, key management, etc.
- Recognition: Originated in the U.S.; validation under the CMVP (U.S./Canada). Widely required or accepted for government use and often expected in regulated sectors.
ISO/IEC 19790 — International Crypto Module Requirements
- What it certifies: International counterpart to FIPS 140 requirements for cryptographic modules.
- Why it matters: Offers globally neutral recognition; many manufacturers pursue both FIPS 140 and ISO/IEC 19790 to maximize market acceptance.
Choosing the Right Certification
Key Factors to Weigh
- Target markets & procurement norms: Some sectors require specific schemes (e.g., FIPS for crypto in North America; CC/PPs across Europe).
- Product type & threat model: Crypto-heavy components often need FIPS/19790; broader security appliances or platforms often fit Common Criteria.
- Time & cost: CC can range from several months to well over a year depending on EAL and scope; FIPS/19790 timelines are often shorter but technically narrower.
Regional Signals (High Level)
- North America: FIPS 140 widely expected for crypto modules in public-sector contexts; CC may be requested for broader solutions.
- Europe: Strong use of Common Criteria (including SOGIS/EUCC developments); PPs influence procurement.
- Asia-Pacific and emerging markets: Increasing alignment to Common Criteria and ISO standards, sometimes with local overlays.
Trends & What’s Next
- Cloud & IoT: CC revisions and PPs increasingly address cloud services, virtualization, and connected devices.
- Crypto alignment: Ongoing work to harmonize FIPS 140-3 and ISO/IEC 19790 eases multi-region strategies.
- Profile-driven evaluations: Industry-authored PPs (e.g., for mobile device management, industrial control) enable clearer, comparable requirements.
- AI/ML: Standards bodies are exploring how to evaluate and assure AI-enabled security functions responsibly.

Frequently Asked Questions
How long does Common Criteria certification take, and what does it cost?
Timelines vary by assurance level and product complexity—typically six to twelve months for EAL2 and a year or more for EAL4. Costs can range from tens of thousands to high six figures for complex, higher-assurance scopes. Plan for lab fees, vendor effort, certification-body review, and time to address findings.
Can a product hold both Common Criteria and FIPS 140 certification?
Yes. Vendors often combine CC (overall product security) with FIPS/ISO 19790 (crypto module validation) to meet diverse customer and regulatory expectations.
What if we patch or release a new version after certification?
Vendors typically run impact analyses. Minor fixes may fit within maintenance without full re-evaluation; major changes generally require re-testing or re-certification.
Are there mutual-recognition agreements?
Yes. Common Criteria certificates benefit from mutual recognition among participating CCRA countries, and FIPS 140 validation is recognized across U.S./Canada via CMVP. Always check for any local add-ons that may still apply.
How do cloud or SaaS products get certified?
Approaches vary. CC can evaluate service security functions (interfaces, data protection, operational controls); some providers certify underlying platforms or specific services against suitable PPs. Work with an experienced lab to scope an evaluation that fits a cloud operating model.